GUIDE BY ETH NETWORK SECURITY
Deploying a non-managed SCION AS in the cloud
supported by Cyberlink and cloudscale
Share this post
The SCION production network has seen significant growth in recent years. Notable examples of its deployment include the Secure Swiss Finance Network (SSFN) and the Secure Swiss Health Network (SSHN), both of which support critical infrastructure and are tailored to members of their respective ecosystems.
Recently, our team at ETH Zurich received exciting news about SCION’s expansion into the cloud. In a joint effort, cloudscale and Cyberlink now offer native SCION connectivity to the production network for all customers. This marks a major milestone: Now, anyone can take advantage of SCION’s advanced networking features directly from their servers at cloudscale, without being part of a larger consortium.
Here, we will walk you through the steps we followed to deploy a SCION Autonomous System (AS) in the cloud supported by Cyberlink and cloudscale – exactly as any customer could.
Your very own SCION Cloud – unmanaged
1. Non-managed SCION access: This option provides a direct SCION link to Cyberlink’s SCION Border Router at cloudscale within the requested SCION ISolation Domain (ISD). Customers choosing this approach are responsible for deploying and managing their own SCION AS services within their Virtual Data Center (VDC).
2. Managed SCION access: In this setup, Cyberlink handles the deployment and management of SCION services on behalf of the customer, offering a more hands-off experience. The managed access makes use of the Anapaya EDGE appliance.
In this post, we describe the non-managed access option, leveraging the open-source SCION services to set up and operate our own AS. The managed option is described in a companion article.
Walkthrough
We created a project within cloudscale to host our SCION-enabled Virtual Data Center (VDC). In parallel, we submitted a request for an Autonomous System Number (ASN) to Anapaya, the authority responsible for assigning SCION ASNs [documentation]. We provided them with details about our deployment scenario, after which they assigned us an ASN and awaited our Certificate Signing Request (CSR).
Once we had this information, we shared it with Cyberlink. They promptly responded with the necessary configuration details for establishing a peering session with their SCION Border Router. These details included:
- cloudscale’s ASN within ISD 64 (the Swiss ISD),
- The virtual interface to be used for the network connecting our Border Router to theirs,
- The IP addresses for both ends of the link—our Border Router and theirs.
At this point, the new network setup was already visible in our cloudscale management console, allowing us to proceed with the configuration.

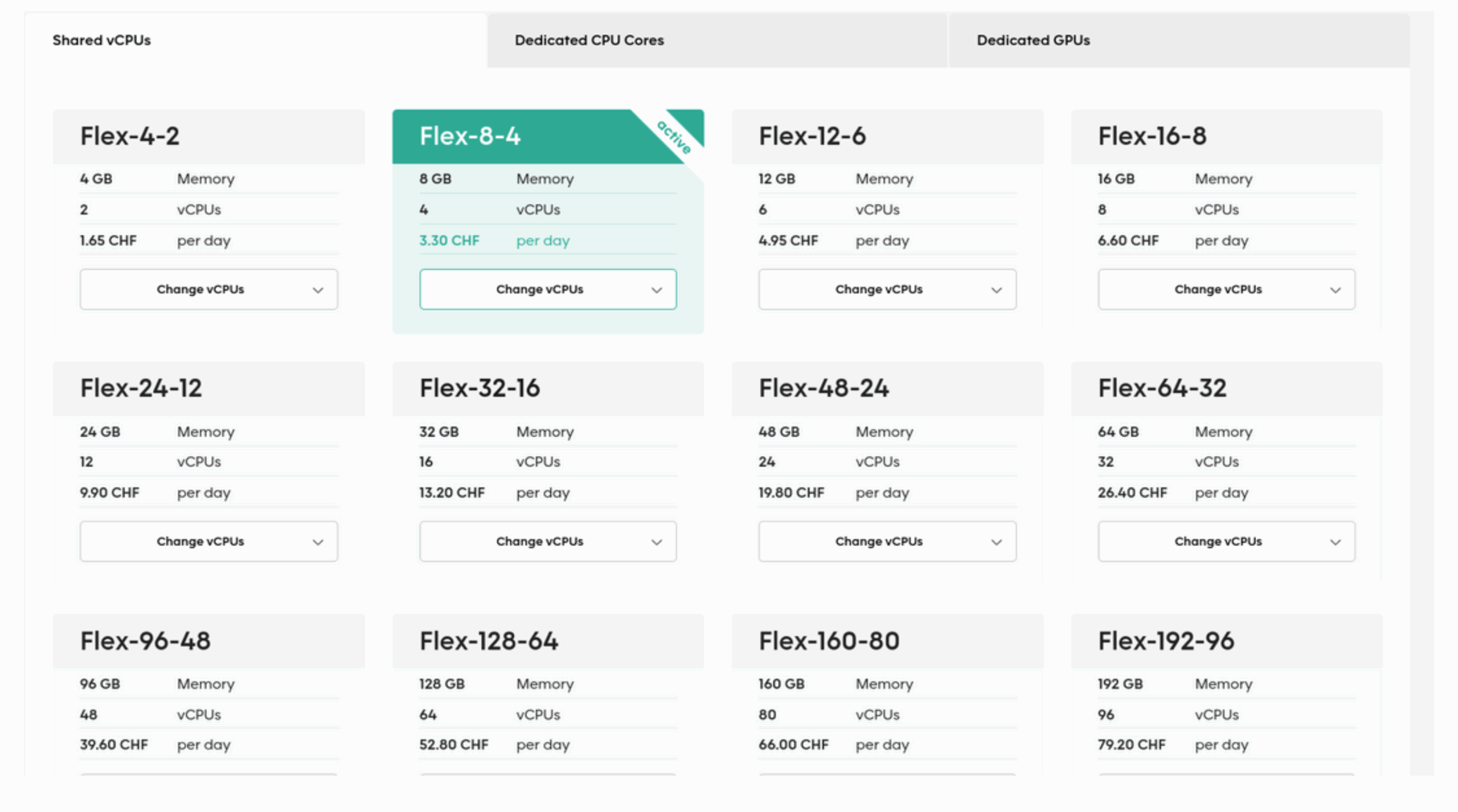
With the peering details in place, we proceeded to install and configure the necessary SCION infrastructure services. To do this, we deployed a virtual machine (VM) within our cloudscale VDC. For our setup, we selected the Flex 8-4 instance type, running Ubuntu 22.04 LTS—a recommended operating system for SCION deployments (Ubuntu 22.04 LTS or newer is advised by the SCION implementation guidelines).
As mentioned earlier, we installed the open-source SCION software. To streamline the deployment process, we used the recently developed SCION Orchestrator, a tool designed to simplify the installation, configuration, and management of SCION services.
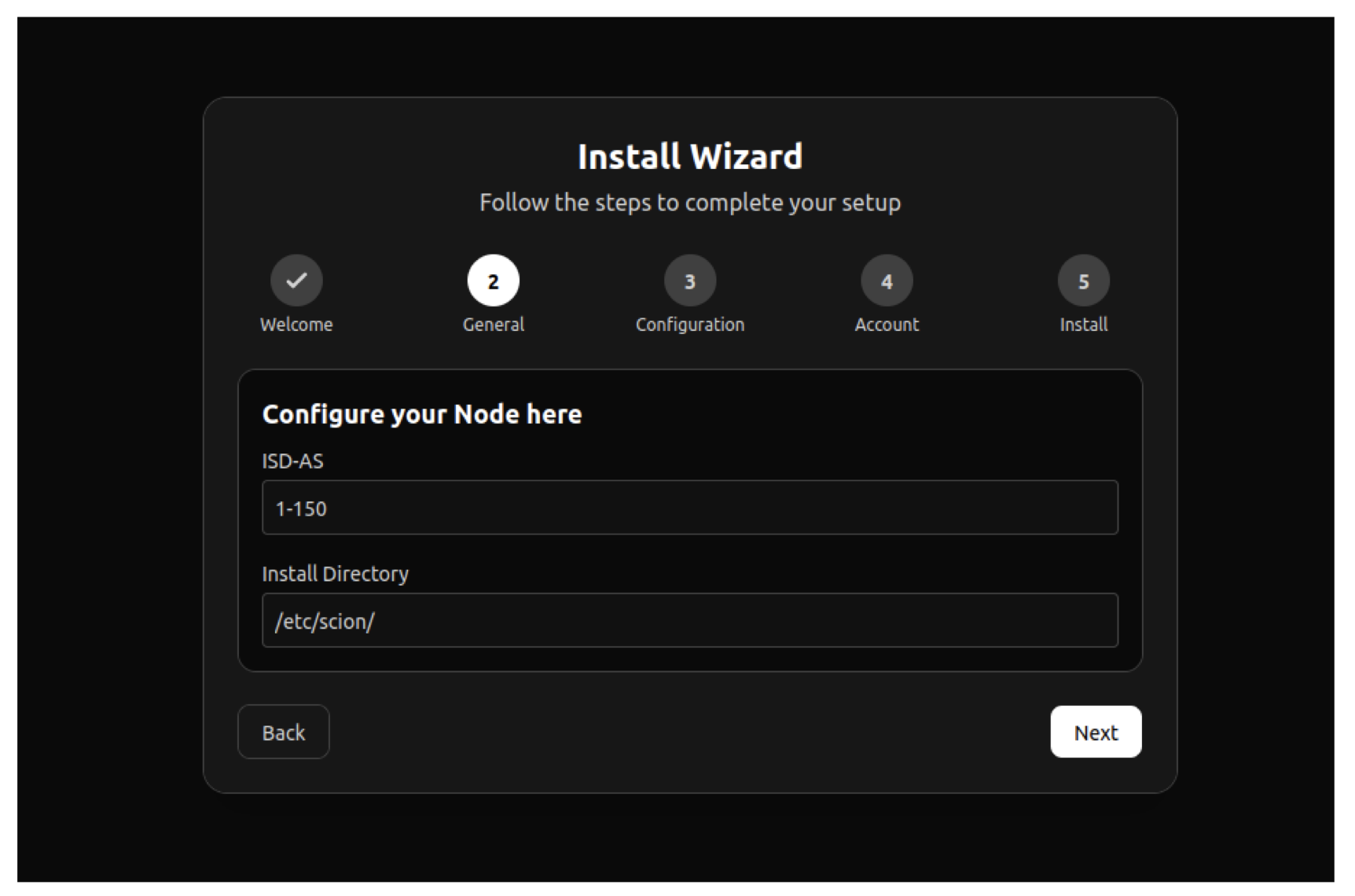
We downloaded the latest release bundle and ran the scion-orchestrator installer. This binary sets up the core SCION services and guides the user to access the web-based interface via https://localhost:8843. Upon first access, the interface launches an installation wizard that walks the user through the initial configuration steps.
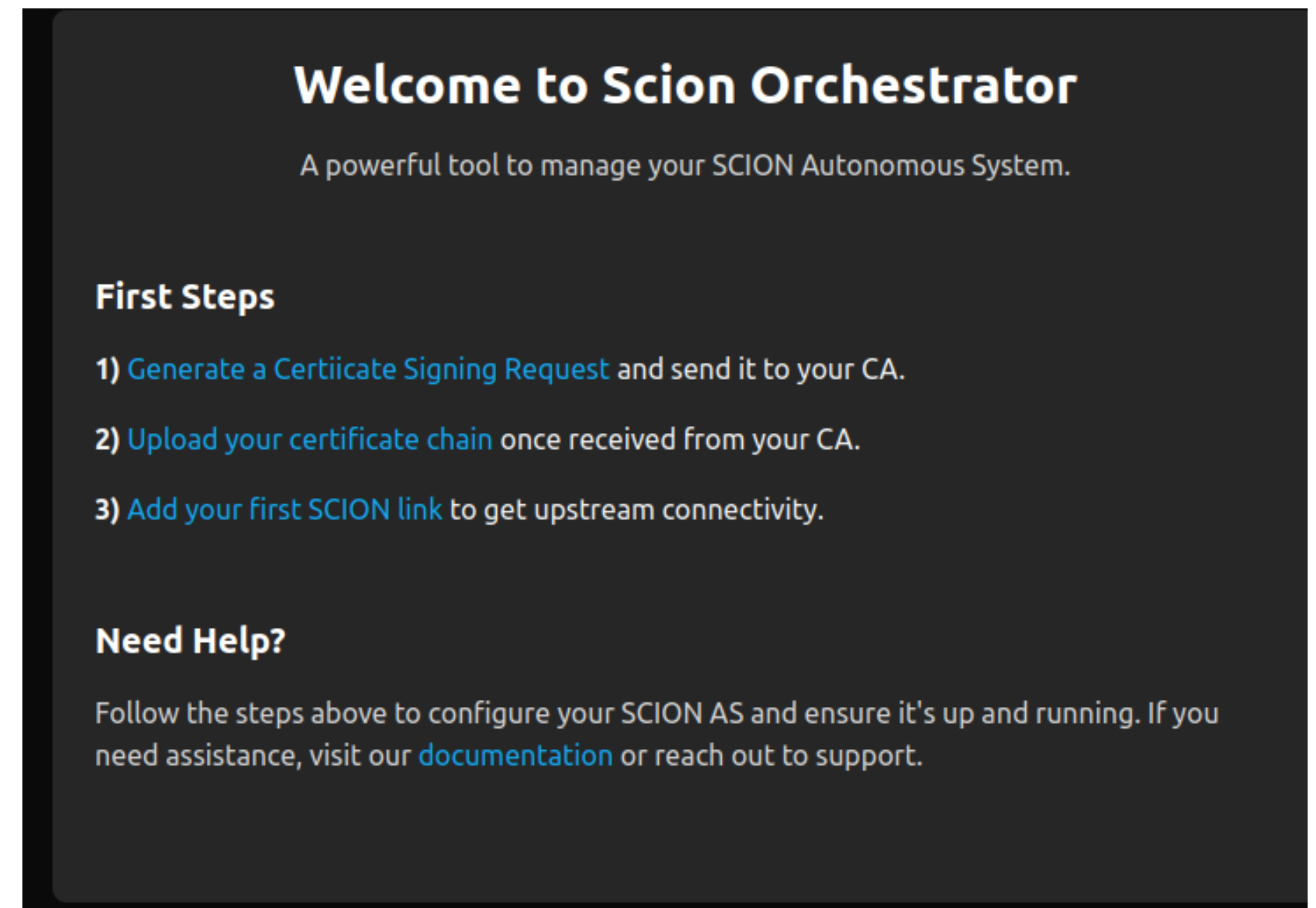
After completing the initial configuration, we reloaded the GUI as instructed. Upon entering our credentials, we gained access to the admin console, which serves as the central interface for managing the SCION Autonomous System (AS). From this console, administrators can configure key aspects of the SCION AS, including service parameters, certificates, and peering relationships.
The next key step is to generate a Certificate Signing Request (CSR). Using the admin console, we filled in the required fields as specified in the official SCION documentation. Once completed, the system generated a .csr file, which we would later submit to the SCION authority for signing (in this case Anapaya).
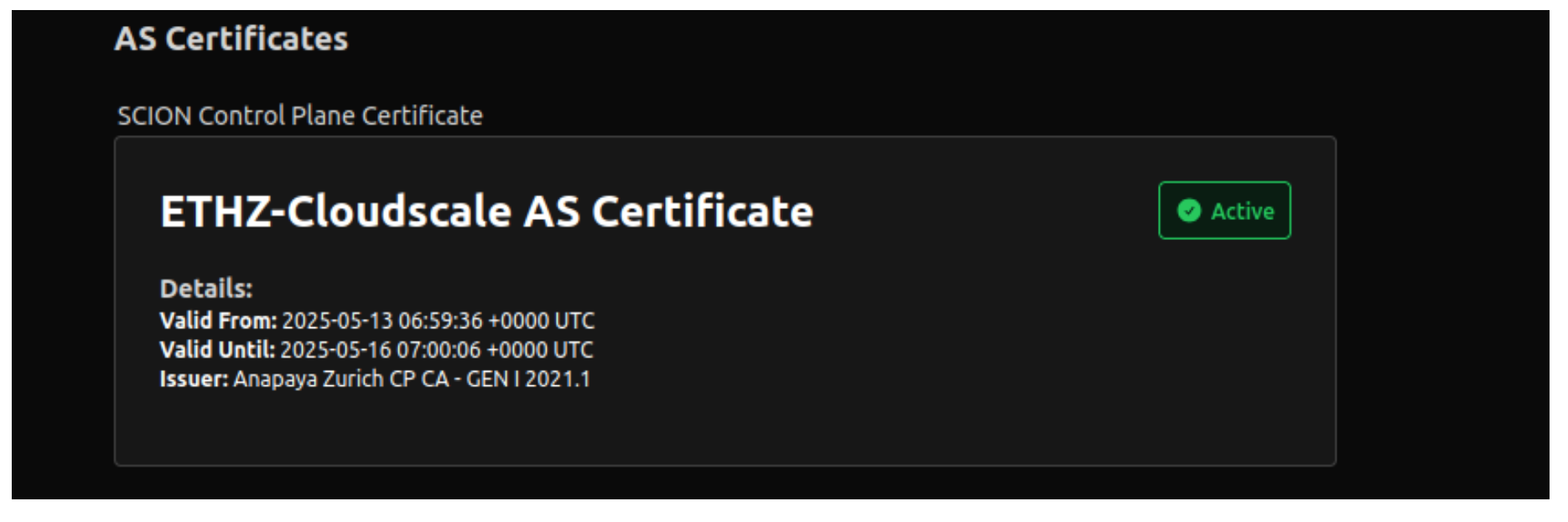
In addition to the CSR, this process also creates the necessary cryptographic material locally, including the private key, required for secure SCION AS operation. We submitted the .csr file to Anapaya, and within a few minutes, they returned our signed SCION certificate. Using the admin console, we uploaded the certificate to complete the trust setup.
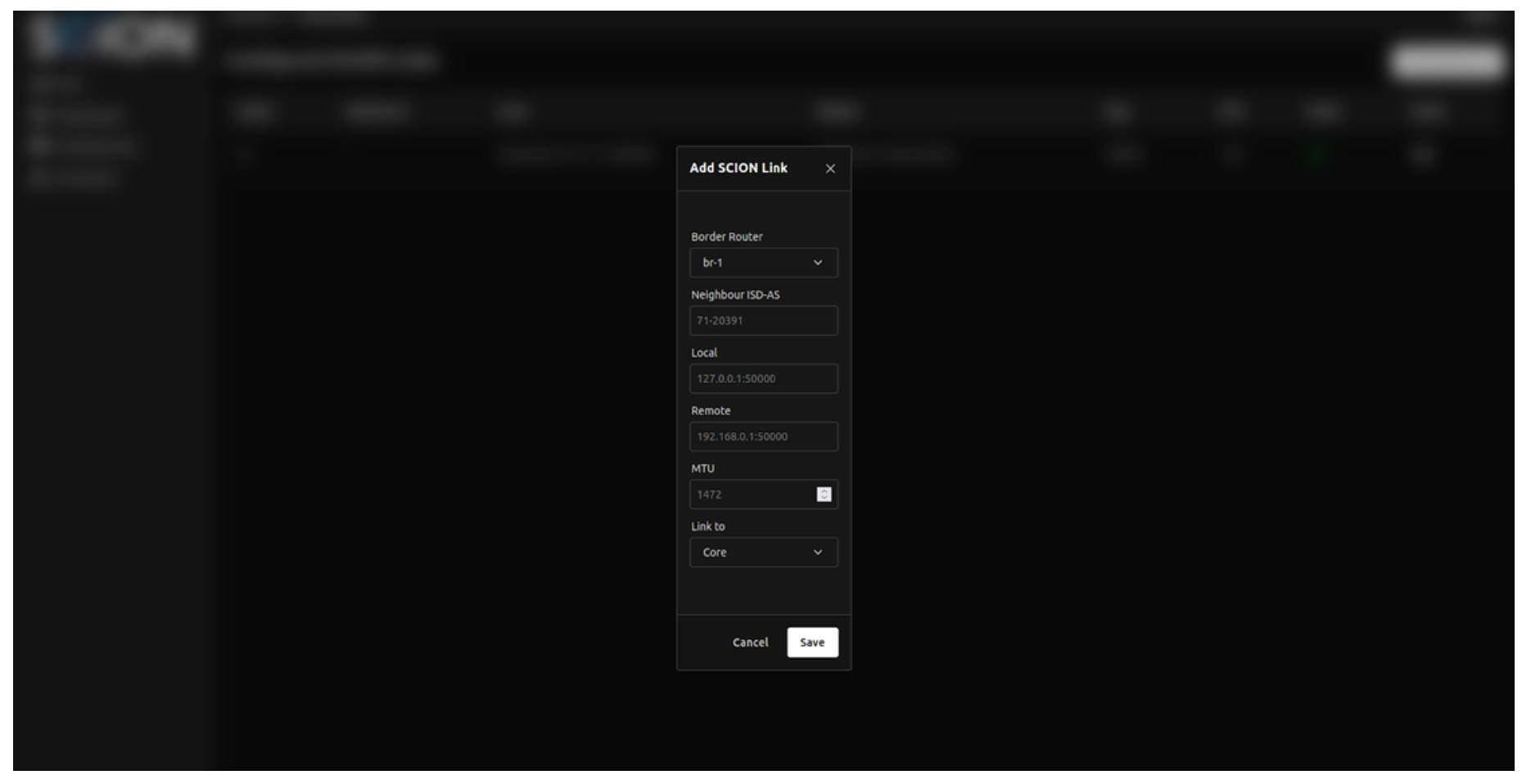
Next, we configured the SCION peering session with cloudscale’s Border Router. To do this, we navigated to the “Connectivity” section in the admin console and selected “Add SCION link.” We filled in the required fields using the configuration details previously provided by Cyberlink and saved the setup. If everything is configured correctly, the link status appears as “Active.”
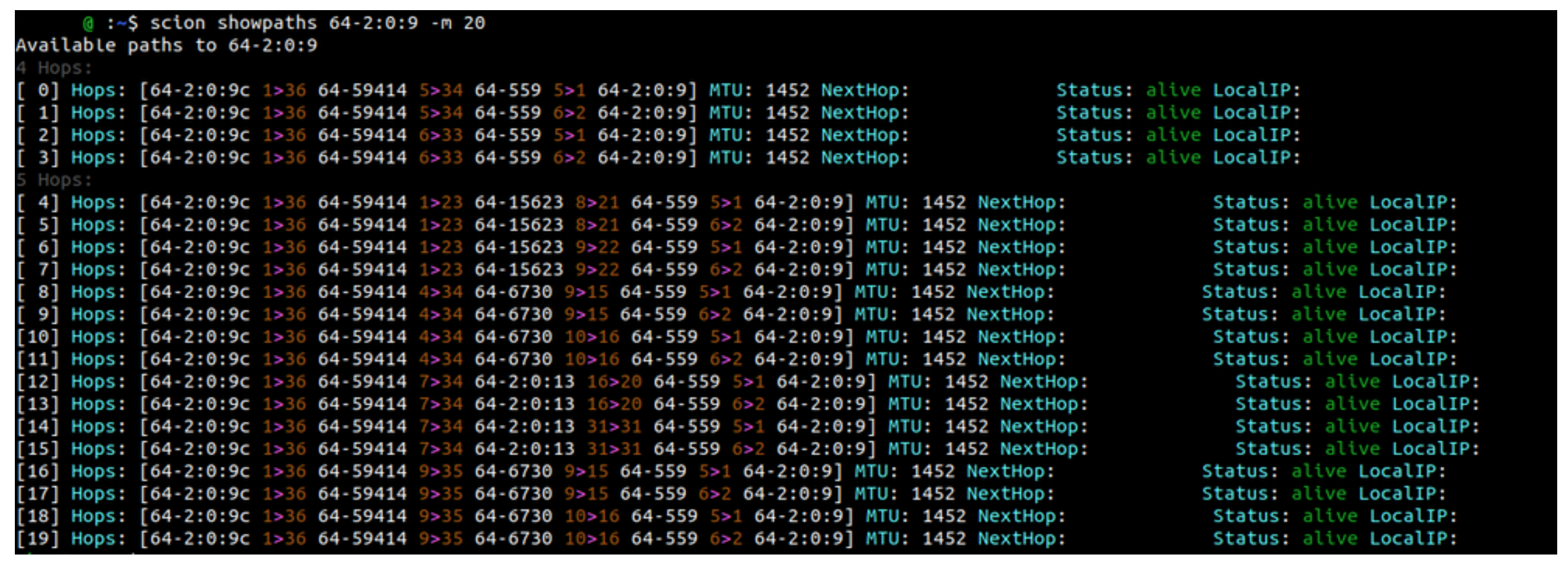
With the link established, our SCION AS was fully operational. We verified connectivity by checking whether we could fetch paths to other ASes in the SCION production network.
Additionally, the orchestrator service will take care of renewing the SCION certificates in the background so that our SCION connectivity is not interrupted by certificate expirations.
Setting up a SCION AS within cloudscale’s infrastructure proved to be a smooth and well-supported process, thanks to the combination of the native SCION connectivity provided by Cyberlink and cloudscale and the tooling provided by the SCION open-source ecosystem. With the help of the SCION Orchestrator, we were able to deploy, configure, and bring our AS online with minimal friction. The ability to independently manage our SCION services while benefiting from cloudscale’s production-grade connectivity opens up exciting possibilities for research, development, and real-world applications.
This setup not only demonstrates the SCION-cloud integration but also lowers the barrier for broader adoption across diverse ecosystems. Once configured, this access offers instant high-availability connectivity to any entity in the SCION ecosystem, similar to a leased line. Although the SCION setup effort requires about 1 hour, secure connectivity can now be established within milliseconds!
Remember to check out our companion post for the Managed SCION access setup. Congrats to cloudscale and Cyberlink for this exciting offering!
About cloudscale:
cloudscale is a leading technology company specializing in cloud infrastructure, with a strong focus on security, performance, and scalability. With data centers in Switzerland and ISO 27001 certification, cloudscale supports its customers in meeting compliance requirements.
About Cyberlink:
Cyberlink is a Swiss managed service provider based in Zürich that specializes in the development and provision of state-of-the-art IT solutions. Cyberlink’s core competencies are innovative cloud solutions, site interconnection, and customized business Internet solutions.
