GUIDE BY ETH NETWORK SECURITY
Deploying a managed SCION AS in the cloud
supported by Cyberlink and cloudscale
Share this post
The SCION production network has seen significant growth in recent years. Notable examples of its deployment include the Secure Swiss Finance Network (SSFN) and the Secure Swiss Health Network (SSHN), both of which support critical infrastructure and are tailored to members of their respective ecosystems.
Recently, our team at ETH Zurich received exciting news about SCION’s expansion into the cloud. In a joint effort, cloudscale and Cyberlink now offer native SCION connectivity to the production network for all customers. This marks a major milestone: Now, anyone can take advantage of SCION’s advanced networking features directly from their servers at cloudscale, without being part of a larger consortium.
Here, we will walk you through the steps we followed to deploy a SCION Autonomous System (AS) in the cloud supported by Cyberlink and cloudscale – exactly as any customer could.
Your very own SCION Cloud – managed
1. Non-managed SCION access: This option provides a direct SCION link to Cyberlink’s SCION Border Router at cloudscale within the requested SCION ISolation Domain (ISD). Customers choosing this approach are responsible for deploying and managing their own SCION AS services within their Virtual Data Center (VDC).
2. Managed SCION access: In this setup, Cyberlink handles the deployment and management of SCION services on behalf of the customer, offering a more hands-off experience. The managed access makes use of the Anapaya EDGE appliance.
In this post, we focus on the Managed SCION Access option, more concretely, on deploying a SCION-enabled endhost within the Managed SCION Access setup. It is particularly well-suited for customers who require performant connectivity and prefer to offload operational overhead. With this approach, customers are not responsible for configuring SCION infrastructure services or managing certificates to keep the SCION AS running.
In a companion post, we explore the non-managed SCION Access option in more detail.
Walkthrough
In parallel, Cyberlink reached out to confirm which cloudscale project should be linked to the SCION access. They also asked if we had any preferences regarding the subnet to be used—specifically, the subnet where we plan to deploy the SCION endhost nodes. By default, Cyberlink assigns a private /24 subnet. Later, we added this private network to the endhost node Virtual Machine (see below).
cloudscale then requested our authorization via email to proceed with linking the SCION access to our project. Once we confirmed, the SCION access appeared in the Networking > Networks section of the cloudscale dashboard.
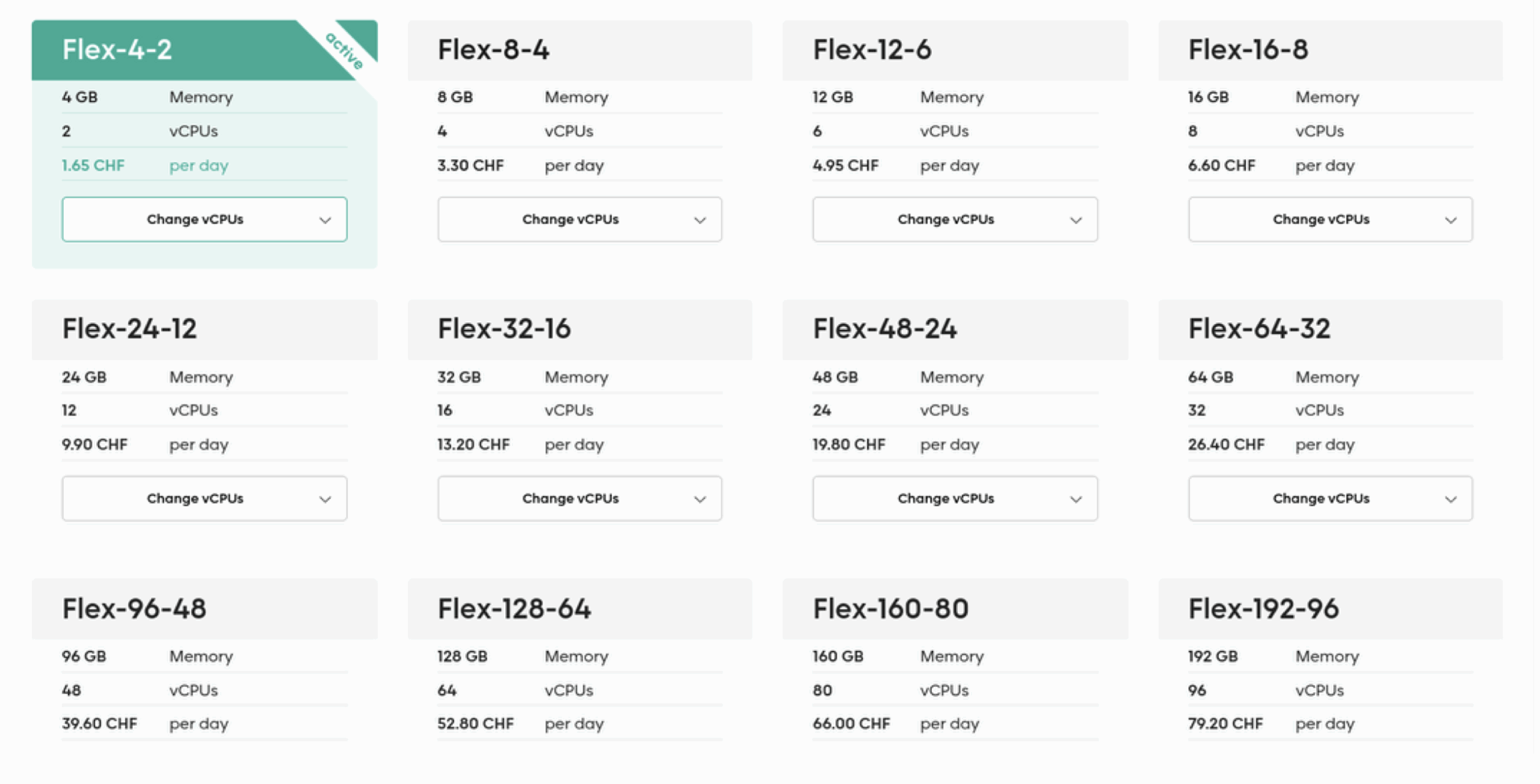
With the network details in place, we proceeded to install and configure the first SCION endhost node. To do this, we deployed a virtual machine (VM) within our cloudscale VDC. For our setup, we selected the Flex 4-2 instance type, running Ubuntu 22.04 LTS—a recommended operating system for SCION deployments (Ubuntu 22.04 LTS or newer is advised by the SCION implementation guidelines).
Finally, we add the private SCION network on the Network Management options. The endhost is configured with an address within that range automatically using DHCP.
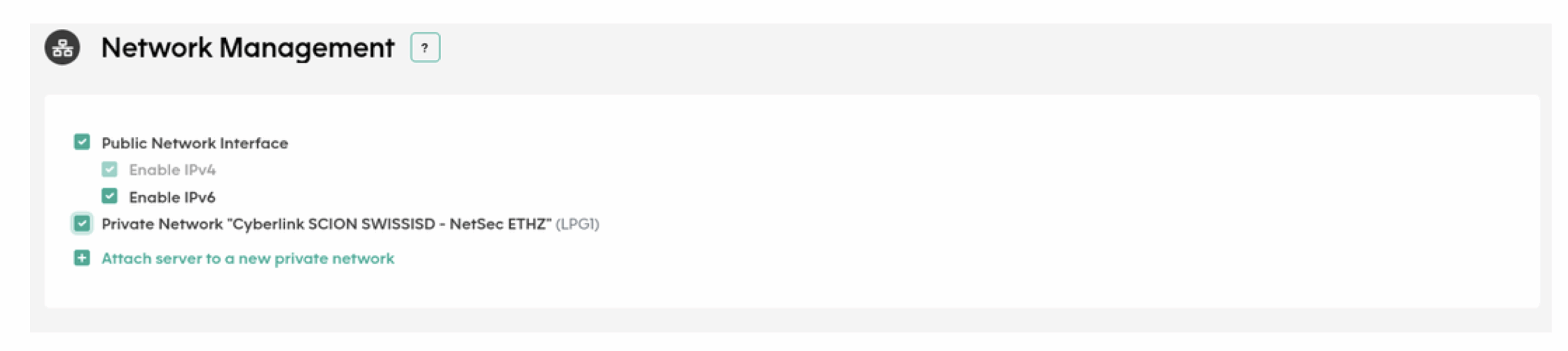
At this stage, Cyberlink provided the interconnection details for the managed SCION node—specifically, the configuration information required on our endhost.
As of the time of writing, the SCION edge appliance does not support a bootstrapping service for native SCION applications running locally. This means the SCION endhost must be configured manually. Fortunately, the process is straightforward. We’re currently working on a seamless and generalizable integration method for SCION endhosts across all existing SCION ecosystems.
We began by installing the SCION endhost stack. You can refer to the official SCION documentation to install the necessary components, i.e., scion-dispatcher, scion-daemon, and scion-tools. Next, we downloaded the latest release of the SCION bootstrapperless configuration tool. After unzipping the archive, we ran the executable from the command line:
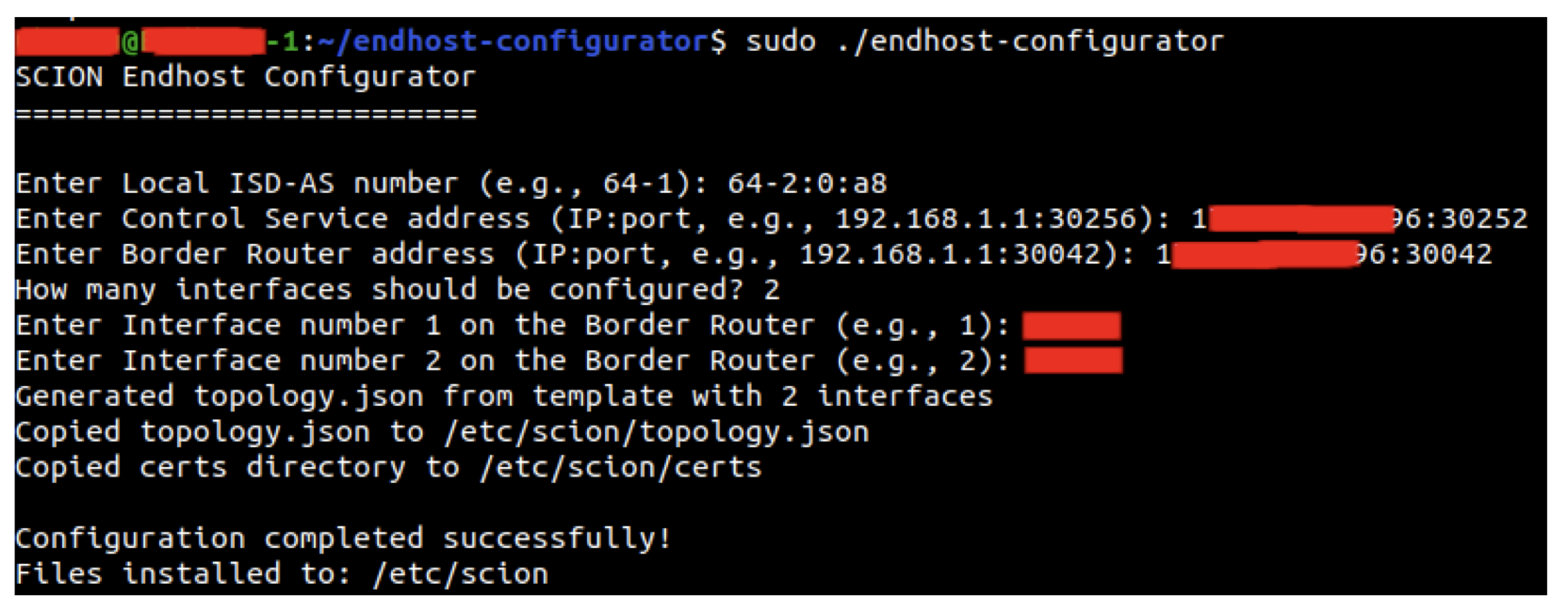
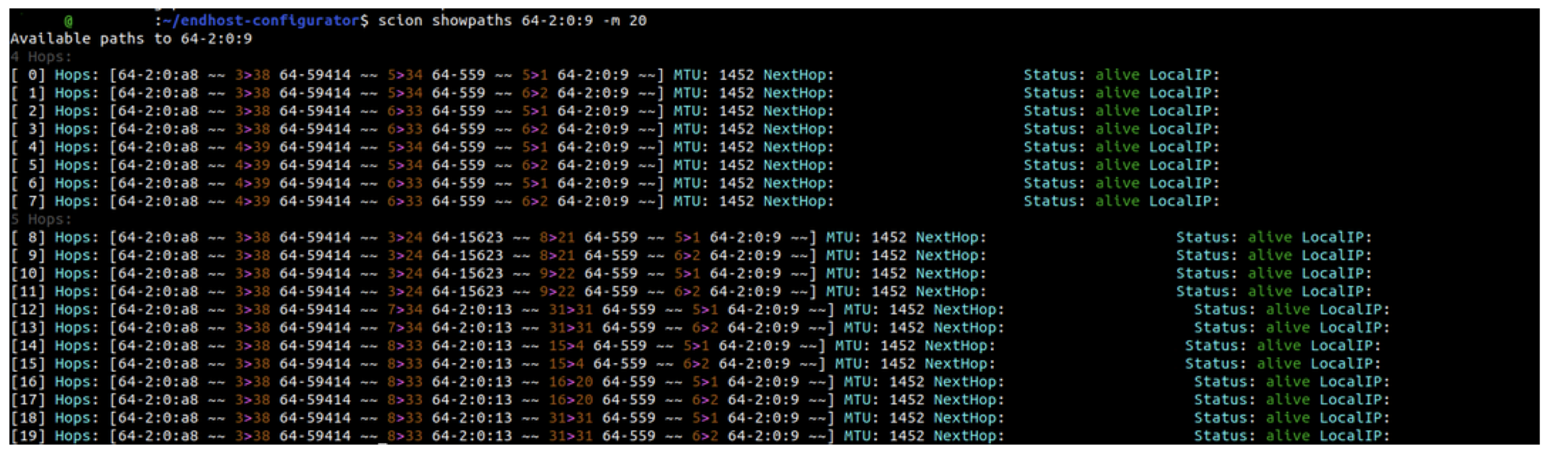
We completed the configuration using the interconnection details previously provided by Cyberlink. Finally, we started the SCION daemon and SCION dispatcher services. To verify connectivity, we used the scion showpaths utility, which confirmed that our endhost could successfully retrieve paths to the SCION production network.
In this post, we focused on deploying a SCION-enabled endhost on the Managed SCION setup. However, SCION-unaware applications can also benefit from the SCION connectivity. One advantage of using the managed deployment with the Anapaya Edge is the fact that traditional SCION-unaware applications can communicate with other remote SCION-unaware applications over SCION-protected communication.
In essence, the Edge announces the configured network prefix to other Edges in the SCION network, and if traffic is sent with a destination address that is reachable via this SCION network, then the Edge encapsulates the packet into a SCION packet and sends it over the best path to the destination Edge, where the IP packet is decapsulated and transparently forwarded to the SCION-unaware destination.
This setup achieves several advantages over a traditional Internet connection:
- Protection from routing attacks
- Fast failover in case of network outages
- Dynamic path optimization across all available paths to the destination, which can result in a lower-latency, lower-loss, and lower-jitter connection than over the Internet
- Geo-fencing through path policy definitions on the Edge
Try it out yourself and experience the benefits of a production-ready SCION environment. Our companion post dives into the Non-managed SCION Access setup.
Congrats to cloudscale and Cyberlink for this exciting offering!
About cloudscale:
cloudscale is a leading technology company specializing in cloud infrastructure, with a strong focus on security, performance, and scalability. With data centers in Switzerland and ISO 27001 certification, cloudscale supports its customers in meeting compliance requirements.
About Cyberlink:
Cyberlink is a Swiss managed service provider based in Zürich that specializes in the development and provision of state-of-the-art IT solutions. Cyberlink’s core competencies are innovative cloud solutions, site interconnection, and customized business Internet solutions.